Your go-to blog for the latest UK Cybersecurity News, Trends, and Developments. Covering Hacking, Data Breaches, Privacy, and Security Standards.
Thursday, 16 March 2017
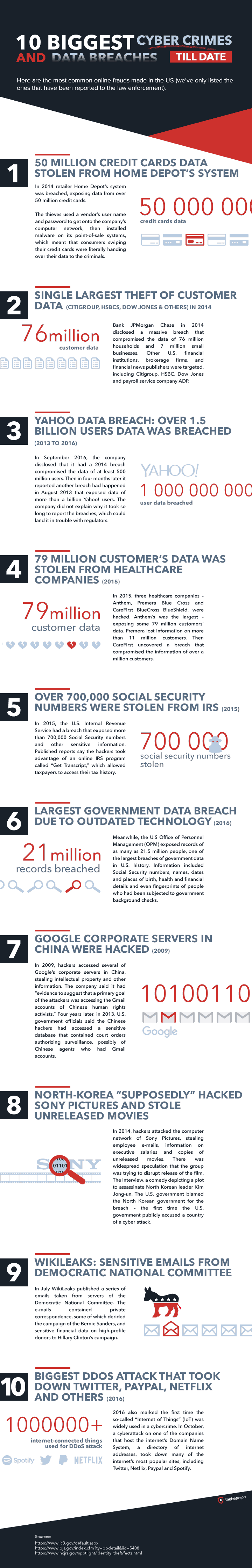
10 Biggest Cyber Crimes and Data Breaches...so far
The good folk at The Best VPN have put together an Infographic summarising ten of the worst "known" cyber attacks and data breaches to date, its a good recap of the high stakes when cyber security goes wrong.


Thursday, 9 March 2017
PCI DSS Penalties & Fines? Cyber Insurance? How to Estimate the Cost of a Payment Card Breach
How much does a payment card breach cost? How large are the potential fines? What happens if we aren't PCI DSS compliant and suffer a cardholder breach?
Those are common unanswered questions which businesses accepting and processing debit and credit card payments rise, businesses which are required to be compliant with the Payment Card Industry Data Security Standard (PCI DSS). In recent years a growing number of UK businesses are taking out cybersecurity insurance, and are more pressingly wanting to know whether their insurance coverage is sufficient enough to cover the cost of a payment card data breach.
Those are common unanswered questions which businesses accepting and processing debit and credit card payments rise, businesses which are required to be compliant with the Payment Card Industry Data Security Standard (PCI DSS). In recent years a growing number of UK businesses are taking out cybersecurity insurance, and are more pressingly wanting to know whether their insurance coverage is sufficient enough to cover the cost of a payment card data breach.
It is not possible to produce a formula or calculator to provide precise payment card breach costs on a per card compromised basis, as no two business payment operations are ever the same, and there are just too many factors that can impact the overall cost of a breach. So instead I have put together the following six pointers to aid the estimation of a payment card breach.
Calculating the Approximate cost of a Payment Card Breach
1. All Payment Card Data breaches must be investigated by PCI qualified Forensic Investigator (PFI). Depending on the technical complexity and scale of the breach, the cost equates to the number of investigator hours and days required, depending that expect to fork out around £20,000 to £100,000 for a PFI. It is worth noting should a business not play ball with the acquiring bank, card brands and card issuers in appointing a PFI, they can remove entire business' capability to take card payments altogether, so there is no choice but to dig deep from the outset upon a data breach discovery.
2. Following the forensic investigation, completion of remediation work and a successful PCI DSS level 1 QSA assessment is required. Remediation work and Qualified Security Assessor (QSA) assessment as a PCI DSS level 1 merchant or processor typically costs up to £100,000, depending on the environment that is in-scope of compliance. This will be a considerable new overhead for environments deemed as PCI DSS level 2, 3 or 4, as these would have previously been self-assessed by the business.
3. The cost per payment card breach is very subjective, however, Verizon's 2015 Data Breach Investigations Report page 30 figure 23, gives a good indication of the "cost per card lost", which I have converted from US dollars.
Optimists should read the left side of the table, pessimists should read the right side of the table.
4. Often there will be a penalty surcharge levied per transaction following a breach, adding an increase to every payment transaction.
5. Reputational damages, loss of customer and client trust in the business and brand, this is a hard figure to quantify, but it is worth noting most cyber insurance policies do not cover any business losses due to reputational damages following data breaches.
6. The Information Commissioners Office (ICO) regards payment card data as Personal Information, which means they can add an up to £500,000 per payment card data breaches. For example in 2015, the ICO fined insurance firm Staysure £175,000 after 5,000 hacked card details used for fraud.
And from May 2018 when the new GDPR data privacy regulation kicks in, potential data protection fines will ramp significantly, especially for large enterprises, with fines of up to 4% of the global turnover of the entire business.
And from May 2018 when the new GDPR data privacy regulation kicks in, potential data protection fines will ramp significantly, especially for large enterprises, with fines of up to 4% of the global turnover of the entire business.
So take the worse case breach scenario, namely a compromise of all payment cards ever stored and processed, apply the above costs, and you should have a worse case scenario ballpark figure. If that number doesn't focus minds and incentivise a robust PCI DSS compliance programme and investment in cyber security, nothing will.
Why Passing a PCI DSS Assesment isn't a 'Get out of Jail Free Card'
No business operating in a PCI DSS compliant state is known to have been breached. Passing a PCI DSS assessment does not mean the business is actually PCI DSS compliant, and it certainly is not a 'get out of jail free' card or carries any weight if a breach occurs. A PCI DSS compliance business means the in-scope of compliance environment and operations meets every single PCI DSS requirement in a continual state of operation, 365 days a year, 24 hours a day, and for every single second.
Wednesday, 1 March 2017
Cyber Security Roundup for February 2017
Printing outs sent Printers open on the Internet
Third party cloud security comes into question after CloudFlare, a popular content delivery network used by more than 5.5 million sites, accidentally leaked customers' sensitive information for months. If you are a CloudFlare customer I strongly advise to change your passwords. The Yahoo’s sale to Verizon has dropped by $350m following Yahoo’s recently reported data breaches. And Sports Direct came in for criticism for not advising its 30,000 staff that their personal details had been hacked.
Back on the technical security front, Google researchers illustrated security weakness in SHA-1. The cryptographic hashing algorithm has not been considered secure since 2010, so the research is a poignant reminder to never use SHA-1 on new configurations, and to review and phase all SHA-1 usage in any existing solutions, such as site-to-site VPNs and within application development, go for SHA-256 or SHA-3 hashing instead.
Back on the technical security front, Google researchers illustrated security weakness in SHA-1. The cryptographic hashing algorithm has not been considered secure since 2010, so the research is a poignant reminder to never use SHA-1 on new configurations, and to review and phase all SHA-1 usage in any existing solutions, such as site-to-site VPNs and within application development, go for SHA-256 or SHA-3 hashing instead.
News
- Major CloudFlare Bug Leaked Sensitive Data from Customers’ Websites
- Verizon Yahoo Deal at Lower Price after Hacks
- Sports Direct 'hid data breach from Staff'
- Google Research Cracks SHA-1 (Cryptographic Hashing Algorithm)
- 40,000 WordPress blogs defaced in Hack Attacks
- Hack of Aberdeen City Council website cost the local authority £10,000
- London Hospital fined £200,000 over fertility Data Breach
- Script-Kiddie Hacker Hijacks Printers through insecure Firewalls
- UK firms 'chronically understaffed' in face of Cyber Threat
- Microsoft release 1 Critical Patch for Adobe Flash Player
- Google reveals bug prior to Microsoft patch
- Only 1.2% of Android devices use latest OS
Subscribe to:
Posts (Atom)