Twitter confirmed 130 celebrity Twitter accounts were targeted in the cyberattack on Wednesday 15th July, with 45 successfully compromised. The hacked Twitter accounts included high profile individuals such as Barack Obama, Elon Musk, Kanye West, Bill Gates, Jeff Bezos, Warren Buffett, Kim Kardashian, and Joe Biden. Their accounts were used to send a tweet to scam Bitcoin out of their millions of followers.
 |
| Scam Social Engineering Tweet sent from Bill Gates' Twitter Account |
Twitter quickly reacted to the hack by taking an unprecedented step of temporarily preventing all verified users from tweeting, including yours truly; I was trying to warn people about the attack but my tweets were repeatedly prevented from posting. Before the scam tweets were taken down more than £80,000 ($100,000) was sent to the scam Tweet's advertised Bitcoin address. The FBI is investigating the incident.
How the Twitter Accounts were Compromised
Twitter said hackers had targeted employees with access to its internal systems and "used this access to take control of many highly-visible (including verified) accounts and Tweet on their behalf". A report by security researcher firm HudsonRock said an advert appeared on a dark web hacker's forum earlier in the week, which offered a service to takeover any Twitter account. The seller said they were able to achieve this by being able to change any Twitter account's linked email address.
The seller was a group or individual that managed to hack their way into Twitter's backend systems, probably by social engineering Twitter's staff, to gain full administration rights at Twitter. This enabled them to provide their buyers with the opportunity to control any Twitter account and to write those accounts' tweets. Hence this nefarious service being bought and then used to acquire Bitcoin via scam messages.
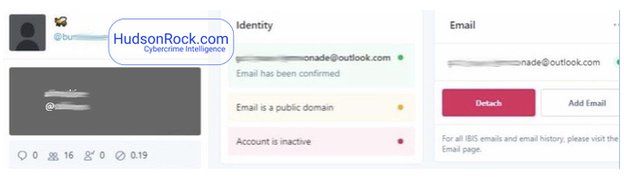 |
| Security researchers at Hudson Rock spotted Twitter Hack advertisement |
Additional Impact?
It is not yet clear whether the hacker(s) stole the Direct Messages (private messages) of the high profile Twitters users, such messages could be used to cause embarrassment and for cyber extortion. The attack appears to be a quick 'smash and grab' money maker, by both the seller to make a quick buck and by the buyer, who used the service to quickly obtain £80k worth of Bitcoin, rather than anything more sinister or sophisticated.
Update as of 18th July 2020
Twitter confirmed the perpetrators used its administration tools to orchestrate the attack and had downloaded data from up to eight of the accounts involved, but said none of these accounts was "verified" high profile accounts.
A New York Times article suggested at least two of the attackers are from England. The attackers successfully manipulated a small number of employees and used their credentials to access Twitter's internal systems
Twitter's statement said "The attackers successfully manipulated a small number of employees and used their credentials to access Twitter's internal systems. We are continuing our investigation of this incident, working with law enforcement, and determining longer-term actions we should take to improve the security of our systems. We're embarrassed, we're disappointed, and more than anything, we're sorry."
Facts Twitter confirmed
Update as of 18th July 2020
Twitter confirmed the perpetrators used its administration tools to orchestrate the attack and had downloaded data from up to eight of the accounts involved, but said none of these accounts was "verified" high profile accounts.
A New York Times article suggested at least two of the attackers are from England. The attackers successfully manipulated a small number of employees and used their credentials to access Twitter's internal systems
Twitter's statement said "The attackers successfully manipulated a small number of employees and used their credentials to access Twitter's internal systems. We are continuing our investigation of this incident, working with law enforcement, and determining longer-term actions we should take to improve the security of our systems. We're embarrassed, we're disappointed, and more than anything, we're sorry."
Facts Twitter confirmed
- Attackers were not able to view previous account passwords, as those are not stored in plain text or available through the tools used in the attack.
- Attackers were able to view personal information including email addresses and phone numbers, which are displayed to some users of our internal support tools.
- In cases where an account was taken over by the attacker, they may have been able to view additional information. Forensic investigation of these activities is still ongoing.
Nigel Thorpe, technical director at SecureAge said the latest Twitter hack exposes the identity and access management vulnerability and the risk of administrator accounts being compromised, leaving data vulnerable. It appears that cybercriminals gained access to Twitter's internal network, then used an admin tool to control the user accounts of prominent individuals and organisations to post fraudulent messages. Using social engineering to gain access to Twitter staff accounts, giving access to data stored in the network.
This incident illustrates the loophole with identity and access management such that if a user account is compromised, data is left unprotected. This loophole can be closed by taking a data-centric approach to security, where information is automatically protected, with authenticated encryption built right into the data. This means that even unencrypted files, when changed or moved, will immediately be encrypted so that, if stolen, they will appear to be garbage to the thief.
A compromised user account still has access to data, but it remains encrypted all the time, even when in use. When copied from its ‘safe’, access-controlled location - even if that's outside the organisation - the data remains encrypted and therefore useless. No ransom, no embarrassing disclosures, no legal action.
Liviu Arsene, Global Cybersecurity Researcher at Bitdefender said with attackers successfully compromising high-profile Twitter accounts that potentially also had two-factor authentication can only point to a coordinated cyberattack at Twitter’s employees and systems. It’s likely this could be a result of attackers exploiting the work-from-home context, in which employees are far more likely to fall prey to scams and spearphishing emails that end up compromising devices and ultimately company systems.
This high-profile Twitter breach could be the result of a spray-and-pray spear-phishing campaign that landed some opportunistic cybercriminals the could potentially be the hack of the year for Twitter. They could have done potentially far more damage. Instead, by delivering a simple Bitcoin scam, we could be looking at attackers that wanted to quickly monetize their access, instead of a highly coordinated and sophisticated operation performed by an APT group.
If this is the case, it’s likely that more companies could potentially be breached as a result of cybercriminals phishing employees. With 50% of organizations not having a plan for supporting and quickly migrating employees and infrastructure to full remote work, we’re probably going to see more data breaches that either exploit employee negligence or infrastructure misconfigurations left behind during the work from home transition.
While large organizations may have strong perimeter security defences, security professionals mostly worry that a potential breach could occur because of attackers exploiting the weakest link in the cybersecurity chain: the human component.
Tony Pepper, CEO of Egress said Twitter has suffered a co-ordinated attack targeting its employees "with access to internal systems and tools" is deeply concerning. However, screenshots obtained from two sources who took over accounts which suggest that this breach was caused by an intentionally malicious insider adds an additional layer of concern and complexity to this saga.
In our 2020 Insider Data Breach, we found that 75% of IT leaders surveyed believe employees have put data at risk intentionally in the past year and this latest breach seems to bear out those beliefs.
So, what can security professionals do to prevent this risk and keep sensitive data out of the reach of malicious threat actors? Organisations have an opportunity to do more by understanding the ‘human layer’ of security, including breach personas and where different risks lie. Technology needs to do more by providing insight into how sensitive data in the organisation is being handled and identifying risks, including human-activated threats.
By spotting the characteristics of a potentially malicious insider and being aware of what they are susceptible to and motivated by, organisations can put the tactics, techniques, and technology in place to mitigate the risk.
This incident illustrates the loophole with identity and access management such that if a user account is compromised, data is left unprotected. This loophole can be closed by taking a data-centric approach to security, where information is automatically protected, with authenticated encryption built right into the data. This means that even unencrypted files, when changed or moved, will immediately be encrypted so that, if stolen, they will appear to be garbage to the thief.
A compromised user account still has access to data, but it remains encrypted all the time, even when in use. When copied from its ‘safe’, access-controlled location - even if that's outside the organisation - the data remains encrypted and therefore useless. No ransom, no embarrassing disclosures, no legal action.
Liviu Arsene, Global Cybersecurity Researcher at Bitdefender said with attackers successfully compromising high-profile Twitter accounts that potentially also had two-factor authentication can only point to a coordinated cyberattack at Twitter’s employees and systems. It’s likely this could be a result of attackers exploiting the work-from-home context, in which employees are far more likely to fall prey to scams and spearphishing emails that end up compromising devices and ultimately company systems.
This high-profile Twitter breach could be the result of a spray-and-pray spear-phishing campaign that landed some opportunistic cybercriminals the could potentially be the hack of the year for Twitter. They could have done potentially far more damage. Instead, by delivering a simple Bitcoin scam, we could be looking at attackers that wanted to quickly monetize their access, instead of a highly coordinated and sophisticated operation performed by an APT group.
If this is the case, it’s likely that more companies could potentially be breached as a result of cybercriminals phishing employees. With 50% of organizations not having a plan for supporting and quickly migrating employees and infrastructure to full remote work, we’re probably going to see more data breaches that either exploit employee negligence or infrastructure misconfigurations left behind during the work from home transition.
While large organizations may have strong perimeter security defences, security professionals mostly worry that a potential breach could occur because of attackers exploiting the weakest link in the cybersecurity chain: the human component.
Tony Pepper, CEO of Egress said Twitter has suffered a co-ordinated attack targeting its employees "with access to internal systems and tools" is deeply concerning. However, screenshots obtained from two sources who took over accounts which suggest that this breach was caused by an intentionally malicious insider adds an additional layer of concern and complexity to this saga.
In our 2020 Insider Data Breach, we found that 75% of IT leaders surveyed believe employees have put data at risk intentionally in the past year and this latest breach seems to bear out those beliefs.
So, what can security professionals do to prevent this risk and keep sensitive data out of the reach of malicious threat actors? Organisations have an opportunity to do more by understanding the ‘human layer’ of security, including breach personas and where different risks lie. Technology needs to do more by providing insight into how sensitive data in the organisation is being handled and identifying risks, including human-activated threats.
By spotting the characteristics of a potentially malicious insider and being aware of what they are susceptible to and motivated by, organisations can put the tactics, techniques, and technology in place to mitigate the risk.
1 comment:
Yes, now twiiter become the hacking point for the hackers
Post a Comment