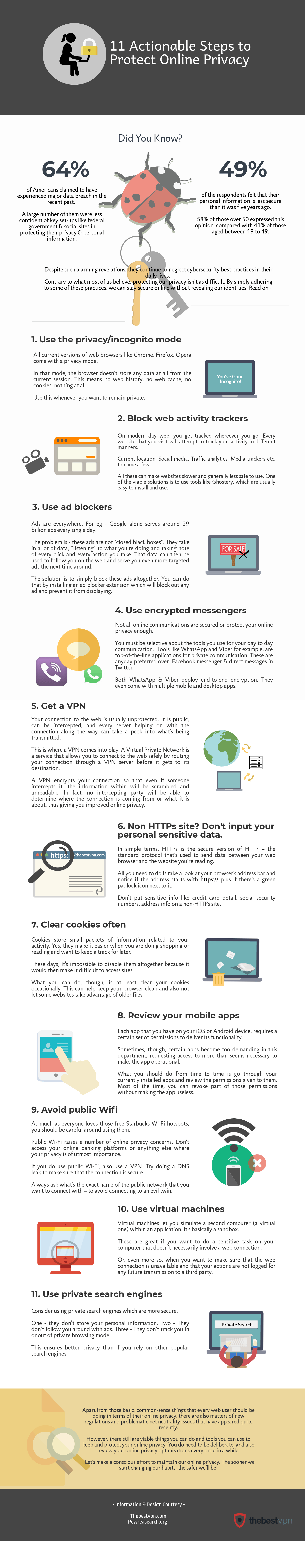
The privacy enthusiasts at The Best VPN have put together crystal clear guidance on protecting your privacy online in one fabulous infographic.
UK cybersecurity analysis and expert commentary on breaches, governance and provable resilience.
18 January 2018
04 January 2018
Meltdown and Spectre: Intel AMD ARM Processor Security Flaws Overview
The New Year has started with a big security bang after new dangerous security vulnerabilities were discovered within Intel, AMD and ARM processors, placing just about every Server, PC, Cloud Service, IoT device, Smartphone and Tablet on the planet at risk.
Google Security Researchers, aka Project Zero, discovered the new computer processor flaws, which they have named 'Meltdown' and 'Spectre' when breaking the bad news on 3rd January 2018. Both Meltdown and Spectre allow an attacker or malware to access privileged information from within what should be a protected area of (kernel) memory. Meaning the potential disclosure of passwords, encryption keys, and confidential data from within virtual environments i.e. where multiple virtual machines are hosted on a single hardware platform.
Meltdown
The Meltdown vulnerability is present on all Intel processors manufactured after 1995 and is the easiest of the two flaws to exploit. This vulnerability exploitation method is known as "rogue data cache load", and can be mitigated by applying the latest operation system patches/updates by Microsoft (KB4056892), Apple, and the various Linux distributions. However, the bad news is according to researchers, the patches are expected to slow (processors) computer systems down between 5% and 30%, given it will be essentially a software patch to fix a hardware defect.
Spectre
The Spectre vulnerability is present on Intel, AMD and ARM processors, and involves two more conceptual methods of attack called 'bounds check bypass' and 'branch target injection', both of which appear to be difficult to execute. Spectre will be much harder to fix by vendors, so expect to wait for the patch releases for it.
It is not currently known if hackers or malware have exploited either Meltdown and Spectre vulnerabilities. Detecting these type of processor exploits is far from easy, as specific processor activity is not typically recorded and checked in centralised security audit log files and audit systems, therefore Meltdown and Spectre exploitations are extremely hard to detect.
Recommended Response
The recommended course of action is to quickly apply the Meltdown and Spectre operation systems\vendor security patches as they are made available, but be mindful of the impact these patches will have on systems, namely, the negative processor performance, and any potential issues with anti-virus software and applications which could impact critical services, especially on servers and within virtual\cloud environments and on low processor powered devices such as IoT devices. Therefore comprehensive patch testing and a rollback plan are essential within businesses environments before Meltdown and Spectre patches are applied, and will help to identify and address any significant performance issues caused by the patches.
Within high-security environments, consider a strategy to replace all (processor) hardware, although a labour intensive and costly approach, it would provide a much higher degree of assurance once fixed processors are released by the chip manufacturers. Hardware replacement may even be a cost-effective approach in the medium to long-term if the performance impact of the patches turns out to be particularly severe.
Google Security Researchers, aka Project Zero, discovered the new computer processor flaws, which they have named 'Meltdown' and 'Spectre' when breaking the bad news on 3rd January 2018. Both Meltdown and Spectre allow an attacker or malware to access privileged information from within what should be a protected area of (kernel) memory. Meaning the potential disclosure of passwords, encryption keys, and confidential data from within virtual environments i.e. where multiple virtual machines are hosted on a single hardware platform.
Meltdown
The Meltdown vulnerability is present on all Intel processors manufactured after 1995 and is the easiest of the two flaws to exploit. This vulnerability exploitation method is known as "rogue data cache load", and can be mitigated by applying the latest operation system patches/updates by Microsoft (KB4056892), Apple, and the various Linux distributions. However, the bad news is according to researchers, the patches are expected to slow (processors) computer systems down between 5% and 30%, given it will be essentially a software patch to fix a hardware defect.
- Meltdown (rogue data cache load - CVE-2017-5754)
- Update your antivirus software before applying Microsoft patches, as Microsoft warned that given their patch changes the design of Windows internal memory management, it could cause issues with installed anti-virus software, therefore the Microsoft update will not install if the anti-virus software is not compatible with the patch. Therefore update your anti-virus application before (the application not the definitions) before applying Microsoft security patches.
- Apple has confirmed all iPhones, iPads, and Mac computers are affected and have released patches for Meltdown in December 2017. Apple has stated there has 'no measurable reduction in the performance of macOS and iOS'.
- Microsoft Surface patches and guidance
- Google have stated patches cause ‘negligible impact on performance’
- See CVE-2017-5754 and meltdownattack.com for further details on Meltdown.
Meltdown Exploit Demo
The Spectre vulnerability is present on Intel, AMD and ARM processors, and involves two more conceptual methods of attack called 'bounds check bypass' and 'branch target injection', both of which appear to be difficult to execute. Spectre will be much harder to fix by vendors, so expect to wait for the patch releases for it.
- Spectre variant 1 (bounds check bypass - CVE-2017-5753
- Spectre variant 2 (branch target injection CVE-2017-5715)
- Apple will release an update for Safari on macOS and iOS in the coming days to mitigate these exploit techniques.
- Google has released patches for Android phones in December 2017
- See CVE-2017-5715, CVE-2017-5753 and meltdownattack.com for further details
For further full technical details see:
- Understanding The Meltdown And Spectre Exploits: Intel, AMD, ARM, and Nvidia
- Meltdown, Spectre Can Be Exploited Through Your Browser
- Latest Patching Details
It is not currently known if hackers or malware have exploited either Meltdown and Spectre vulnerabilities. Detecting these type of processor exploits is far from easy, as specific processor activity is not typically recorded and checked in centralised security audit log files and audit systems, therefore Meltdown and Spectre exploitations are extremely hard to detect.
Recommended Response
The recommended course of action is to quickly apply the Meltdown and Spectre operation systems\vendor security patches as they are made available, but be mindful of the impact these patches will have on systems, namely, the negative processor performance, and any potential issues with anti-virus software and applications which could impact critical services, especially on servers and within virtual\cloud environments and on low processor powered devices such as IoT devices. Therefore comprehensive patch testing and a rollback plan are essential within businesses environments before Meltdown and Spectre patches are applied, and will help to identify and address any significant performance issues caused by the patches.
Within high-security environments, consider a strategy to replace all (processor) hardware, although a labour intensive and costly approach, it would provide a much higher degree of assurance once fixed processors are released by the chip manufacturers. Hardware replacement may even be a cost-effective approach in the medium to long-term if the performance impact of the patches turns out to be particularly severe.
02 January 2018
Cyber Security Roundup for December 2017
UK supermarket giant Morrisons, lost a landmark data breach court case in December after a disgruntled Morrisons employee had stolen and posted the personal records of 100,000 co-workers online, the supermarket chain was held liable for the data breach by the UK High Court. The High Court ruling now allows those affected to claim compensation for the "upset and distress" caused. Morrisons said it believed it should not have been held responsible and would be appealing against the decision. If the appeal is lost it could open up the possibility of further class action lawsuits cases by individuals. Pending the GDPR becoming law in May 2018, such a court ruling sets a legal precedent for individuals to claim damages after personal data losses by companies through the courts as well. After May 2018, the GDPR grants individuals the right sue companies for damages following personal data breaches. So we can expect 'ambulance chasers' lawyers to pick up on this aspect of the GDPR, with class action lawsuits following data breaches, it well could become the new "P.P.I. industry"
Any businesses or individuals using Kaspersky should be aware the UK National Cyber Security Centre has warned government agencies against using the Russian supplier’s products and services, which follows a ban by US government departments in November. Barclays responded to the warning by stopping their free offering of Kaspersky anti-virus products to its customers. 2017 saw Cyber Security become a political football, so it is no real surprise that the UK and US once again blamed North Korea for the devasting WannaCry attacks earlier in the year, personally, I blame poor patch management and hackers, not the North Korea cyber army!
Nadine Dorries MP got herself in hot water after trying to defend now former political colleague Damian Green, following claims of Mr.Green accessed porn on his Parliment computer. This was activity was reported by a retired Police officer, which was said to be a breach of the data protection act. Nadine tweeted "my staff log onto my computer on my desk with my login everyday" to suggest anyone could have used Damian Green's PC to access the illicit websites. This led to widespread condemnation and a warning by ICO to MPs on password sharing.
The fact illicit websites were not blocked by Parliament systems is one concerning lack security issue, but the flagrant disregard for basic cybersecurity by government MPs is gobsmacking, especially when you consider they are supposed to be understanding the risk and setting laws to protect UK citizens from cyber attacks and data breaches. Its another "slap palm on head" after the last UK Prime Minister announced he wanted to ban encryption.
2017 has seen huge rises in cryptocurrencies values, which has placed cryptocurrency brokers and user crypto coin wallets in the sights of cybercriminals. This month mining platform NiceHash was breached by hackers, who stole £51 million worth of Bitcoin and Bitcoin exchange Youbit, which lets people buy and sell Bitcoins and other virtual currencies, shut down and filed for bankruptcy after losing 17% of its assets in the cyber-attacks. I think we can expect further cryptocurrencies attacks in 2018 given the cryptocurrency bubble is yet to burst.
Faked LinkedIn profiles are nothing new, however, the German Intelligence Agency (BfV) said it had spotted China were using faked LinkedIn profiles to connect with and gather information on German officials and politicians, which is an interesting development.
Finally, Hackers were reported as taking advantage of poorly secured systems at UK private schools, and it was claimed hackers could turn off heating systems at UK schools and military bases.
NEWSAny businesses or individuals using Kaspersky should be aware the UK National Cyber Security Centre has warned government agencies against using the Russian supplier’s products and services, which follows a ban by US government departments in November. Barclays responded to the warning by stopping their free offering of Kaspersky anti-virus products to its customers. 2017 saw Cyber Security become a political football, so it is no real surprise that the UK and US once again blamed North Korea for the devasting WannaCry attacks earlier in the year, personally, I blame poor patch management and hackers, not the North Korea cyber army!
Nadine Dorries MP got herself in hot water after trying to defend now former political colleague Damian Green, following claims of Mr.Green accessed porn on his Parliment computer. This was activity was reported by a retired Police officer, which was said to be a breach of the data protection act. Nadine tweeted "my staff log onto my computer on my desk with my login everyday" to suggest anyone could have used Damian Green's PC to access the illicit websites. This led to widespread condemnation and a warning by ICO to MPs on password sharing.
The fact illicit websites were not blocked by Parliament systems is one concerning lack security issue, but the flagrant disregard for basic cybersecurity by government MPs is gobsmacking, especially when you consider they are supposed to be understanding the risk and setting laws to protect UK citizens from cyber attacks and data breaches. Its another "slap palm on head" after the last UK Prime Minister announced he wanted to ban encryption.
2017 has seen huge rises in cryptocurrencies values, which has placed cryptocurrency brokers and user crypto coin wallets in the sights of cybercriminals. This month mining platform NiceHash was breached by hackers, who stole £51 million worth of Bitcoin and Bitcoin exchange Youbit, which lets people buy and sell Bitcoins and other virtual currencies, shut down and filed for bankruptcy after losing 17% of its assets in the cyber-attacks. I think we can expect further cryptocurrencies attacks in 2018 given the cryptocurrency bubble is yet to burst.
Faked LinkedIn profiles are nothing new, however, the German Intelligence Agency (BfV) said it had spotted China were using faked LinkedIn profiles to connect with and gather information on German officials and politicians, which is an interesting development.
Finally, Hackers were reported as taking advantage of poorly secured systems at UK private schools, and it was claimed hackers could turn off heating systems at UK schools and military bases.
- NCSC warns UK government agencies on use of Kaspersky Products and Services
- Morrisons Supermarket held Liable after Employee Leaks Data
- Data breach at PayPal's TIO Networks unit affects 1.6 million Customers
- Hackers target Private UK Schools
- Hackers could turn off UK School and Military Base Heating Systems
- UK & US Blame North Korea for WannaCry
- German Spy Agency warns of Chinese LinkedIn Espionage
- Nadine Dorries MP under scrutiny for comments about Password Sharing
- Three plead guilty to creating Mirai IoT Botnet Malware
- Cryptocurrency thieves steal £51 million of Bitcoin from Mining Platform
- Microsoft releases 19 Critical Security Updates for IE/Edge, Office, & Windows
- Adobe releases fixes for Flash Player
- Updates Address Security Vulnerabilities in Apache Struts versions 2.5 to 2.5.14
- Cisco Patches Multiple Vulnerabilities in WebEx Platforms
- Apple Release Security Updates shortly after releasing another KRACK Fix
- TLS exploit Capitalises on 19-year-old vulnerability; Vendors issue Patch
- TeamViewer releases Emergency Patch for Permissions Flaw
- VMware Fixes Bugs in vCenter Service Appliance and Hypervisors
- Threat Group APT-C-23 still active, releases GnatSpy Mobile Malware
- Microsoft bug CVE-2017-11882 Exploited to deliver Loki Information Stealer